 Operation and Maintenance
Operation and Maintenance
 Linux Operation and Maintenance
Linux Operation and Maintenance
 Analysis of user password storage mechanism in Linux system
Analysis of user password storage mechanism in Linux system
Analysis of user password storage mechanism in Linux system
Mar 20, 2024 pm 04:27 PM
Analysis of user password storage mechanism in Linux system
In Linux system, the storage of user password is one of the very important security mechanisms. This article will analyze the storage mechanism of user passwords in Linux systems, including the encrypted storage of passwords, the password verification process, and how to securely manage user passwords. At the same time, specific code examples will be used to demonstrate the actual operation process of password storage.
1. Encrypted storage of passwords
In the Linux system, user passwords are not stored in the system in plain text, but are encrypted and saved. The commonly used password encryption algorithm in Linux systems is SHA-512 (SHA-256 can also be used). In the Linux system, the user's password is stored in the /etc/shadow file, which stores the user's account information, including the encrypted password, password expiration time, password last modification time, etc.
The following is the content of an example /etc/shadow file:
root:$6$xld94ij$BW0RfSx9WLNAWia7D5PQwx/dNnhTgy8f3W6/vobqEmmhVUISZoL5EwrF8RTXA8xRztRGtUjLzxyBnUqVoJk7Z.:18474:0:99 999:7::: user1:$6$du065TO$9v6.LU3F8JbLVQ7FEQEfkrQ.Zd8dxR.Vl5ohZ9uiXG4lF8k1OHkRTrqtzc5RpaC2mvM5KpIe7YH2zUL3MOUEO1:18474:0:99999:7:::
Among them, the first field represents the user name, and the second field is Encrypted password. It can be seen that the password has been encrypted into a garbled code, so even if the /etc/shadow file is leaked, it will be difficult for hackers to restore the user's password.
2. Password verification process
When a user logs in to the system, the system will verify whether the password entered by the user is correct. The process of verifying the password is actually to encrypt the password entered by the user according to the same encryption algorithm, and then compare it with the password in the /etc/shadow file. If the two are consistent, the verification is successful and the user is allowed to log in; otherwise, the verification fails and the user is refused to log in.
The following is a simple password verification code example, written in Python:
import crypt
import getpass
def validate_password(username, password):
with open('/etc/shadow', 'r') as f:
for line in f:
if line.startswith(username ':'):
shadow_entry = line.split(':')
encrypted_password = shadow_entry[1]
salt = encrypted_password.split('$')[2]
new_encrypted_password = crypt.crypt(password, '$6$' salt '$')
if new_encrypted_password == encrypted_password:
return True
else:
return False
return False
username = input("Enter username: ")
password = getpass.getpass("Enter password: ")
if validate_password(username, password):
print("Password is correct. Logging in...")
else:
print("Password is incorrect. Please try again.")3. Securely manage user passwords
Managing user passwords is a very important security issue. First, simple passwords should be avoided and complex passwords containing uppercase and lowercase letters, numbers, and special characters are recommended. Secondly, change your password regularly to avoid using the same password for a long time. Also, passwords should not be stored in clear text anywhere, including in code.
In Linux systems, administrators can use the passwd command to modify the user password. This command will automatically encrypt the user password and store it in the /etc/shadow file. In addition, you can use some specialized password management tools to help manage user passwords, such as KeePass, LastPass, etc.
Summary:
The user password storage mechanism in the Linux system is a very important security mechanism. Through encrypted storage and strict verification process, the user password is protected from being easily leaked. Administrators need to regularly review password policies to ensure the security of user passwords. At the same time, users also need to pay attention to the security of their passwords and avoid using simple passwords and storing plain text passwords in unsafe places.
Through the analysis and code examples of this article, I hope readers will have a deeper understanding of the storage mechanism of user passwords in Linux systems to improve system security.
[Number of words: 798 words]
The above is the detailed content of Analysis of user password storage mechanism in Linux system. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Postman Integrated Application on CentOS
May 19, 2025 pm 08:00 PM
Postman Integrated Application on CentOS
May 19, 2025 pm 08:00 PM
Integrating Postman applications on CentOS can be achieved through a variety of methods. The following are the detailed steps and suggestions: Install Postman by downloading the installation package to download Postman's Linux version installation package: Visit Postman's official website and select the version suitable for Linux to download. Unzip the installation package: Use the following command to unzip the installation package to the specified directory, for example /opt: sudotar-xzfpostman-linux-x64-xx.xx.xx.tar.gz-C/opt Please note that "postman-linux-x64-xx.xx.xx.tar.gz" is replaced by the file name you actually downloaded. Create symbols
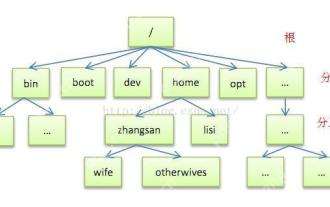 Detailed introduction to each directory of Linux and each directory (reprinted)
May 22, 2025 pm 07:54 PM
Detailed introduction to each directory of Linux and each directory (reprinted)
May 22, 2025 pm 07:54 PM
[Common Directory Description] Directory/bin stores binary executable files (ls, cat, mkdir, etc.), and common commands are generally here. /etc stores system management and configuration files/home stores all user files. The root directory of the user's home directory is the basis of the user's home directory. For example, the home directory of the user user is /home/user. You can use ~user to represent /usr to store system applications. The more important directory /usr/local Local system administrator software installation directory (install system-level applications). This is the largest directory, and almost all the applications and files to be used are in this directory. /usr/x11r6?Directory for storing x?window/usr/bin?Many
 Where is the pycharm interpreter?
May 23, 2025 pm 10:09 PM
Where is the pycharm interpreter?
May 23, 2025 pm 10:09 PM
Setting the location of the interpreter in PyCharm can be achieved through the following steps: 1. Open PyCharm, click the "File" menu, and select "Settings" or "Preferences". 2. Find and click "Project:[Your Project Name]" and select "PythonInterpreter". 3. Click "AddInterpreter", select "SystemInterpreter", browse to the Python installation directory, select the Python executable file, and click "OK". When setting up the interpreter, you need to pay attention to path correctness, version compatibility and the use of the virtual environment to ensure the smooth operation of the project.
 The difference between programming in Java and other languages ??Analysis of the advantages of cross-platform features of Java
May 20, 2025 pm 08:21 PM
The difference between programming in Java and other languages ??Analysis of the advantages of cross-platform features of Java
May 20, 2025 pm 08:21 PM
The main difference between Java and other programming languages ??is its cross-platform feature of "writing at once, running everywhere". 1. The syntax of Java is close to C, but it removes pointer operations that are prone to errors, making it suitable for large enterprise applications. 2. Compared with Python, Java has more advantages in performance and large-scale data processing. The cross-platform advantage of Java stems from the Java virtual machine (JVM), which can run the same bytecode on different platforms, simplifying development and deployment, but be careful to avoid using platform-specific APIs to maintain cross-platformity.
 After installing Nginx, the configuration file path and initial settings
May 16, 2025 pm 10:54 PM
After installing Nginx, the configuration file path and initial settings
May 16, 2025 pm 10:54 PM
Understanding Nginx's configuration file path and initial settings is very important because it is the first step in optimizing and managing a web server. 1) The configuration file path is usually /etc/nginx/nginx.conf. The syntax can be found and tested using the nginx-t command. 2) The initial settings include global settings (such as user, worker_processes) and HTTP settings (such as include, log_format). These settings allow customization and extension according to requirements. Incorrect configuration may lead to performance issues and security vulnerabilities.
 MySQL installation tutorial teach you step by step the detailed steps for installing and configuration of mySQL step by step
May 23, 2025 am 06:09 AM
MySQL installation tutorial teach you step by step the detailed steps for installing and configuration of mySQL step by step
May 23, 2025 am 06:09 AM
The installation and configuration of MySQL can be completed through the following steps: 1. Download the installation package suitable for the operating system from the official website. 2. Run the installer, select the "Developer Default" option and set the root user password. 3. After installation, configure environment variables to ensure that the bin directory of MySQL is in PATH. 4. When creating a user, follow the principle of minimum permissions and set a strong password. 5. Adjust the innodb_buffer_pool_size and max_connections parameters when optimizing performance. 6. Back up the database regularly and optimize query statements to improve performance.
 Comparison between Informix and MySQL on Linux
May 29, 2025 pm 11:21 PM
Comparison between Informix and MySQL on Linux
May 29, 2025 pm 11:21 PM
Informix and MySQL are both popular relational database management systems. They perform well in Linux environments and are widely used. The following is a comparison and analysis of the two on the Linux platform: Installing and configuring Informix: Deploying Informix on Linux requires downloading the corresponding installation files, and then completing the installation and configuration process according to the official documentation. MySQL: The installation process of MySQL is relatively simple, and can be easily installed through system package management tools (such as apt or yum), and there are a large number of tutorials and community support on the network for reference. Performance Informix: Informix has excellent performance and
 Experience in participating in VSCode offline technology exchange activities
May 29, 2025 pm 10:00 PM
Experience in participating in VSCode offline technology exchange activities
May 29, 2025 pm 10:00 PM
I have a lot of experience in participating in VSCode offline technology exchange activities, and my main gains include sharing of plug-in development, practical demonstrations and communication with other developers. 1. Sharing of plug-in development: I learned how to use VSCode's plug-in API to improve development efficiency, such as automatic formatting and static analysis plug-ins. 2. Practical demonstration: I learned how to use VSCode for remote development and realized its flexibility and scalability. 3. Communicate with developers: I have obtained skills to optimize VSCode startup speed, such as reducing the number of plug-ins loaded at startup and managing the plug-in loading order. In short, this event has benefited me a lot and I highly recommend those who are interested in VSCode to participate.





