What is the overall design method of java Dubbo architecture?
Apr 27, 2023 pm 09:52 PM1. Dubbo calling relationship description
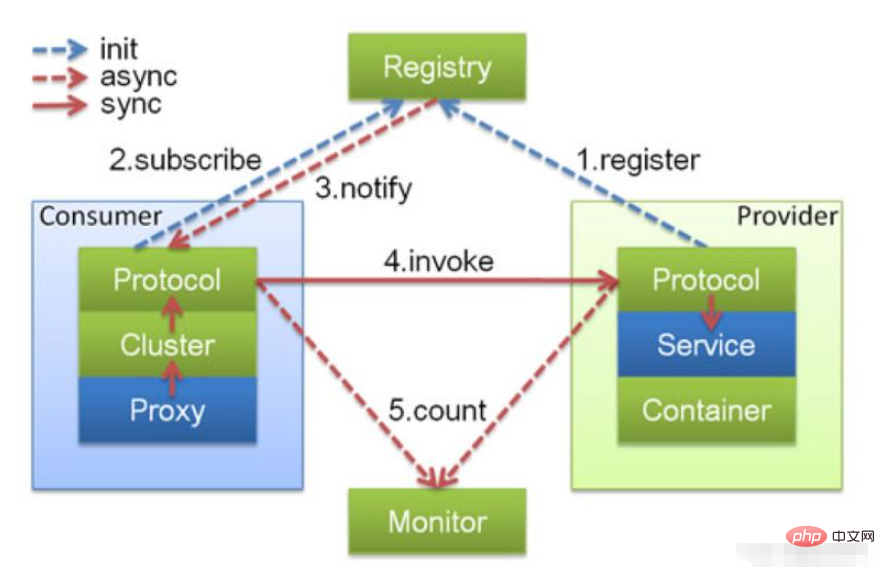
Here It is mainly composed of four parts:
● Provider: the service provider that exposes the serviceProtocol: responsible for the protocol interaction data between the provider and the consumer
Service: the real business service Information can be understood as interfaces and implementations
Container: Dubbo's operating environment
● Consumer: The service consumer that calls the remote service
Protocol: Responsible for the protocol interaction data between the provider and the consumer
Cluster: Perceives the list information on the provider side
Proxy: It can be understood as the provider's service calling proxy, which takes over the interface calling logic in the Consumer
● Register: Registration center, used for service discovery and routing configuration, etc. Work, providers and consumers will be registered here
● Monitor: used for data statistics on providers and consumers, such as call frequency, number of successes and failures, etc.
● When the consumer side starts, it senses the provider information by listening to the provider list, and When the provider changes, the consumer is promptly notified through the registration center
● The consumer initiates a request through the Proxy module;
● The consumer uses the Cluster module to select the real provider to be called;
● Consumer Use the Protocol in the Consumer to send the information to the provider;
● The provider processes consumer information through the Protocol module;
● Finally, the provider's Service handles the processing
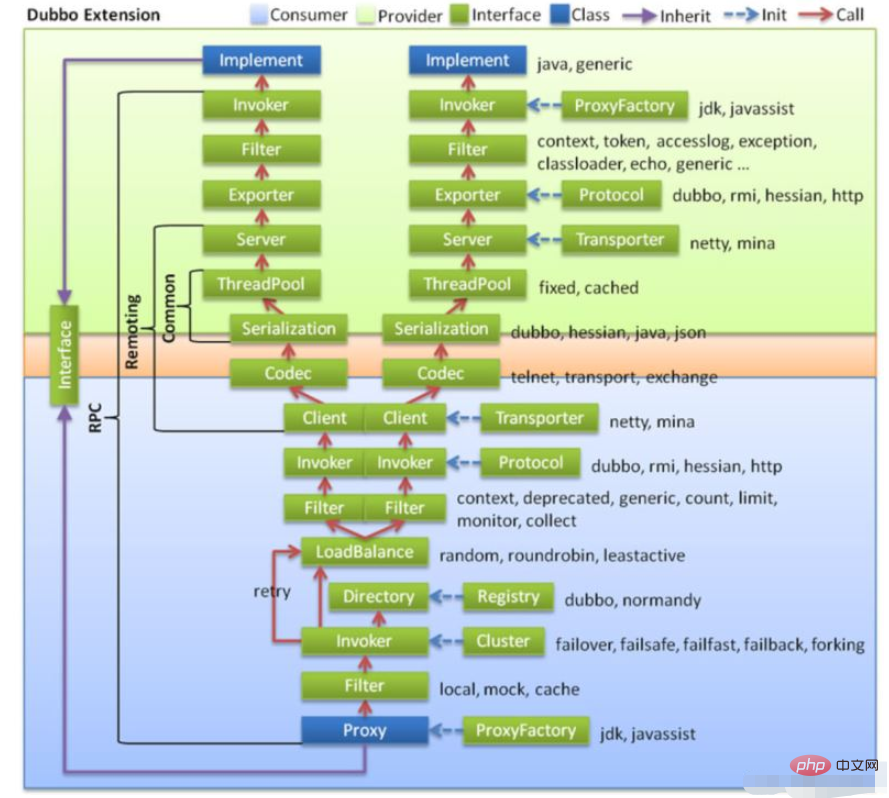
The overall calling process is as follows:
● Consumers call methods through the Interface, unified It is handed over to the Proxy on the consumer side and the proxy object is created through ProxyFactory. The javassist technology of jdk is used here● It is handed over to the Filter module to make unified filtering requests
● Next is the most important Invoker calling logic
○ Read information from the configuration through Directory, and finally obtain all Invokers through the list method
○ Through the Cluster module, select the Invoker list according to the selected specific routing rules
○ Through the LoadBalance module, according to the load balancing policy Select a specific Invoker to handle the request
○ If an error occurs during execution, and the retry mechanism is configured in the Consumer stage, the execution will be retried
● Continue to use the Filter to encapsulate the execution function before and after, and the Invoker selects a specific Invoker Execute the protocol
● The client performs encoding and serialization, and then sends the data
● Reach the Server layer in the Provider to decode and serialize the received data
● Use Exporter to select the executor
● Let the Filter perform a provider-side filtering and reach the Invoker executor
● Call the specific implementation of the interface through the Invoker, and then return the result
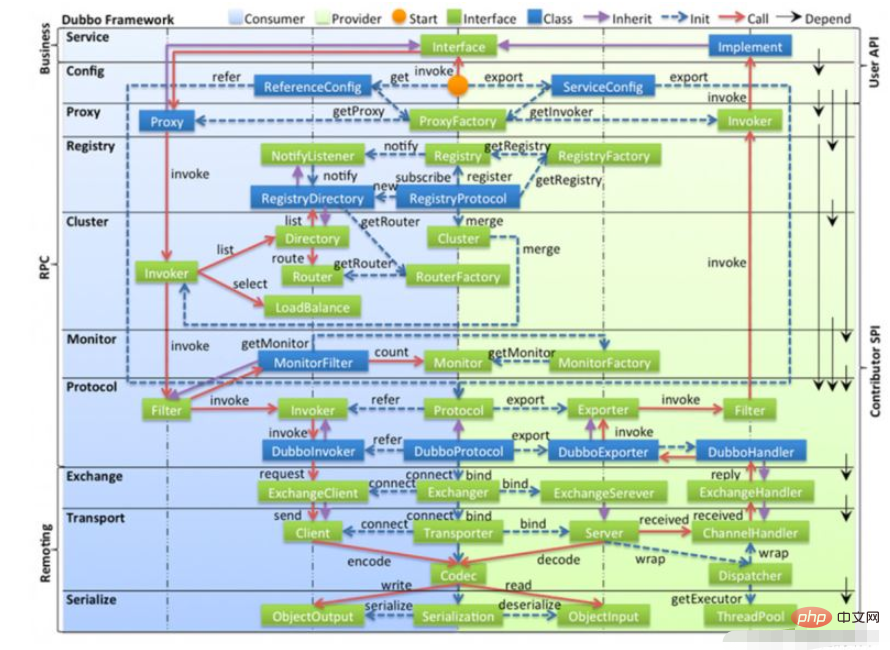
Legend:
● In the figure, the light blue background on the left is the interface used by the service consumer, and the light green background on the right is the interface used by the service provider. The interface located on the central axis is used by both parties.● The figure is divided into ten layers from top to bottom. Each layer has one-way dependencies. The black arrow on the right represents the dependency relationship between layers. Each layer can be stripped off the upper layer and reused. Among them, the Service and Config layers is an API, and all other layers are SPI
● The green blocks in the picture are extension interfaces, and the blue blocks are implementation classes. The picture only shows the implementation classes used to associate each layer
● The blue blocks in the picture are The dotted line is the initialization process, that is, the assembly chain at startup. The solid red line is the method calling process, that is, the runtime call chain. The purple arrow is inheritance. The subclass can be regarded as the same node of the parent class. The text on the line is the call Methods.
The following is a layered introduction
1. Business logic layer
● Service business layer: including business code such as interfaces and implementation classes
2. RPC layer: remote procedure call layer
● config configuration layer, which provides configuration to the outside world. ServiceConfig and ReferenceConfig are the core, which can directly initialize the configuration class or parse the configuration file
● Proxy service agent layer, whether it is a producer or a consumer, the framework will generate a proxy class. The whole process is transparent to the upper layer, and the business layer Remote calls are insensitive
● Register registration center layer, which encapsulates the registration and discovery of service addresses, with the service URL as the center
● Cluster routing layer (cluster fault-tolerant layer), provides routing and load for multiple providers Balanced, and it bridges the registration center with Invoker as the center
● Monitor monitoring layer, RPC call-related information, such as the number of calls, failure situations, call time and other statistical information will be completed in this layer
● Protocol remote The call layer, which encapsulates RPC calls, whether it is service exposure or service reference, is responsible for the entire life cycle of Invoker as the main function entrance in Protocol. All models in Dubbo move closer to Invoker
3. Rmoting layer: Remote data transmission layer
● Exchange information exchange layer, encapsulates the request and response mode, converts the request from synchronous to asynchronous
● Transport network transport layer, unifies the network transmission interface, such as Netty and mina unified into one network Transmission interface
● Serialize data serialization layer, responsible for managing the serialization and deserialization of data transmission in the entire framework
The above is the detailed content of What is the overall design method of java Dubbo architecture?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to iterate over a Map in Java?
Jul 13, 2025 am 02:54 AM
How to iterate over a Map in Java?
Jul 13, 2025 am 02:54 AM
There are three common methods to traverse Map in Java: 1. Use entrySet to obtain keys and values at the same time, which is suitable for most scenarios; 2. Use keySet or values to traverse keys or values respectively; 3. Use Java8's forEach to simplify the code structure. entrySet returns a Set set containing all key-value pairs, and each loop gets the Map.Entry object, suitable for frequent access to keys and values; if only keys or values are required, you can call keySet() or values() respectively, or you can get the value through map.get(key) when traversing the keys; Java 8 can use forEach((key,value)->
 Comparable vs Comparator in Java
Jul 13, 2025 am 02:31 AM
Comparable vs Comparator in Java
Jul 13, 2025 am 02:31 AM
In Java, Comparable is used to define default sorting rules internally, and Comparator is used to define multiple sorting logic externally. 1.Comparable is an interface implemented by the class itself. It defines the natural order by rewriting the compareTo() method. It is suitable for classes with fixed and most commonly used sorting methods, such as String or Integer. 2. Comparator is an externally defined functional interface, implemented through the compare() method, suitable for situations where multiple sorting methods are required for the same class, the class source code cannot be modified, or the sorting logic is often changed. The difference between the two is that Comparable can only define a sorting logic and needs to modify the class itself, while Compar
 How to handle character encoding issues in Java?
Jul 13, 2025 am 02:46 AM
How to handle character encoding issues in Java?
Jul 13, 2025 am 02:46 AM
To deal with character encoding problems in Java, the key is to clearly specify the encoding used at each step. 1. Always specify encoding when reading and writing text, use InputStreamReader and OutputStreamWriter and pass in an explicit character set to avoid relying on system default encoding. 2. Make sure both ends are consistent when processing strings on the network boundary, set the correct Content-Type header and explicitly specify the encoding with the library. 3. Use String.getBytes() and newString(byte[]) with caution, and always manually specify StandardCharsets.UTF_8 to avoid data corruption caused by platform differences. In short, by
 JavaScript Data Types: Primitive vs Reference
Jul 13, 2025 am 02:43 AM
JavaScript Data Types: Primitive vs Reference
Jul 13, 2025 am 02:43 AM
JavaScript data types are divided into primitive types and reference types. Primitive types include string, number, boolean, null, undefined, and symbol. The values are immutable and copies are copied when assigning values, so they do not affect each other; reference types such as objects, arrays and functions store memory addresses, and variables pointing to the same object will affect each other. Typeof and instanceof can be used to determine types, but pay attention to the historical issues of typeofnull. Understanding these two types of differences can help write more stable and reliable code.
 What is the 'static' keyword in Java?
Jul 13, 2025 am 02:51 AM
What is the 'static' keyword in Java?
Jul 13, 2025 am 02:51 AM
InJava,thestatickeywordmeansamemberbelongstotheclassitself,nottoinstances.Staticvariablesaresharedacrossallinstancesandaccessedwithoutobjectcreation,usefulforglobaltrackingorconstants.Staticmethodsoperateattheclasslevel,cannotaccessnon-staticmembers,
 Using std::chrono in C
Jul 15, 2025 am 01:30 AM
Using std::chrono in C
Jul 15, 2025 am 01:30 AM
std::chrono is used in C to process time, including obtaining the current time, measuring execution time, operation time point and duration, and formatting analysis time. 1. Use std::chrono::system_clock::now() to obtain the current time, which can be converted into a readable string, but the system clock may not be monotonous; 2. Use std::chrono::steady_clock to measure the execution time to ensure monotony, and convert it into milliseconds, seconds and other units through duration_cast; 3. Time point (time_point) and duration (duration) can be interoperable, but attention should be paid to unit compatibility and clock epoch (epoch)
 How does a HashMap work internally in Java?
Jul 15, 2025 am 03:10 AM
How does a HashMap work internally in Java?
Jul 15, 2025 am 03:10 AM
HashMap implements key-value pair storage through hash tables in Java, and its core lies in quickly positioning data locations. 1. First use the hashCode() method of the key to generate a hash value and convert it into an array index through bit operations; 2. Different objects may generate the same hash value, resulting in conflicts. At this time, the node is mounted in the form of a linked list. After JDK8, the linked list is too long (default length 8) and it will be converted to a red and black tree to improve efficiency; 3. When using a custom class as a key, the equals() and hashCode() methods must be rewritten; 4. HashMap dynamically expands capacity. When the number of elements exceeds the capacity and multiplies by the load factor (default 0.75), expand and rehash; 5. HashMap is not thread-safe, and Concu should be used in multithreaded
 What is a ReentrantLock in Java?
Jul 13, 2025 am 02:14 AM
What is a ReentrantLock in Java?
Jul 13, 2025 am 02:14 AM
ReentrantLock provides more flexible thread control in Java than synchronized. 1. It supports non-blocking acquisition locks (tryLock()), lock acquisition with timeout (tryLock(longtimeout, TimeUnitunit)) and interruptible wait locks; 2. Allows fair locks to avoid thread hunger; 3. Supports multiple condition variables to achieve a more refined wait/notification mechanism; 4. Need to manually release the lock, unlock() must be called in finally blocks to avoid resource leakage; 5. It is suitable for scenarios that require advanced synchronization control, such as custom synchronization tools or complex concurrent structures, but synchro is still recommended for simple mutual exclusion requirements.






