Found a total of 10000 related content

5 Bootstrap Password Strength Meter/Complexity Demos
Article Introduction:Enhance Password Security with Bootstrap Password Strength Meters: 5 Demos to Boost User Protection
Strong passwords are crucial for online account security. Help your users create stronger passwords with these 5 Bootstrap password strength meter de
2025-02-22
comment 0
324

Build a Simple Password Strength Checker
Article Introduction:Providing instant feedback is the in-thing right now. Why limit yourself to checking usernames and email addresses? Why not extend this to provide quick visual feedback about the strength of the password the user has input? Today, we'll take a look a
2025-03-09
comment 0
904

Developing a Password Strength Plugin with jQuery
Article Introduction:Passwords remain a cornerstone of online security, even with the rise of multi-factor authentication. This article guides you through creating a robust jQuery password strength plugin using the zxcvbn library. This plugin helps users generate stron
2025-02-22
comment 0
860

php regex for password strength
Article Introduction:To determine the strength of the password, it is necessary to combine regular and logical processing. The basic requirements include: 1. The length is no less than 8 digits; 2. At least containing lowercase letters, uppercase letters, and numbers; 3. Special character restrictions can be added; in terms of advanced aspects, continuous duplication of characters and incremental/decreasing sequences need to be avoided, which requires PHP function detection; at the same time, blacklists should be introduced to filter common weak passwords such as password and 123456; finally it is recommended to combine the zxcvbn library to improve the evaluation accuracy.
2025-07-03
comment 0
512

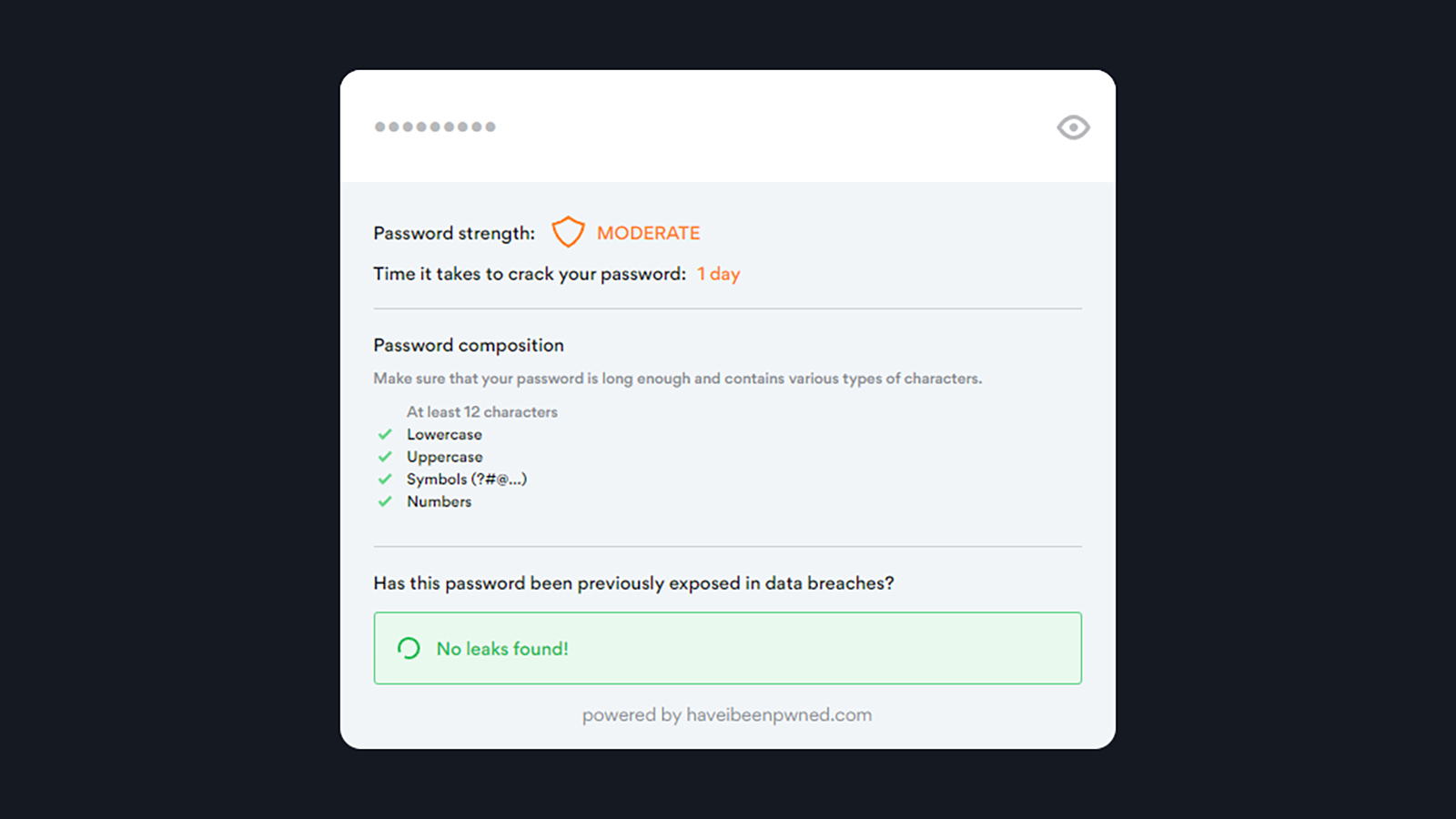
How to check your password strength—and what to do about it
Article Introduction:Passwords remain crucial despite the rise of biometric logins. Managing numerous accounts and passwords across various online services demands robust security measures. This article explores how to create and safeguard strong, unique passwords.
Cra
2025-02-25
comment 0
572

How to reset database password in Navicat?
Article Introduction:Navicat password reset: Confirm reset target: Navicat connection password or database user password. Navicat connection password reset: Modify the connection configuration in Navicat. Reset the database user password (taking MySQL as an example): Use a user with permission to log in to the server and execute the SQL statement SET PASSWORD. Pay attention to permission issues, password strength and root password forgetting. Other database types are different, so you need to consult the document. It is recommended to use a password manager to store the database password securely.
2025-04-08
comment 0
939

How secure is Navicat's password?
Article Introduction:Navicat's password security relies on the combination of symmetric encryption, password strength and security measures. Specific measures include: using SSL connections (provided that the database server supports and correctly configures the certificate), regularly updating Navicat, using more secure methods (such as SSH tunnels), restricting access rights, and most importantly, never record passwords.
2025-04-08
comment 0
1056

Password Checker - JavaScript
Article Introduction:This program opens a window in the browser. User inputs a password its level of strength. It runs from a single .html file containing 72 lines of code, including both the HTML structure and embedded JavaScript for functionality.
This example is for
2024-10-24
comment 0
895

How Debian ensures GitLab's data security
Article Introduction:Data security is crucial to deploy GitLab on Debian systems. This article outlines the key strategies and measures to ensure the security of GitLab data: Strengthen password policy: Use the PAM module to implement strict password policies, enforce the combination requirements of minimum password length, numbers, upper and lower case letters and special characters, and improve password strength. Secure SSH configuration: Force authentication of SSH key pairs to eliminate password login and reduce security risks. Prohibit root users from logging in remotely through SSH to enhance system security. Strictly limit login of empty passwords to increase the difficulty of cracking. Fine firewall management: rationally configure the iptables firewall and only open necessary ports (such as HTTP)
2025-04-12
comment 0
787

how to change your password on Windows 10
Article Introduction:There are three main ways to change passwords on Windows 10, depending on the account type and usage scenario. 1. Local accounts can be modified through "Settings" → "Account" → "Login Options" → "Password" → "Change". You need to enter the current password and set a new password that meets the complexity; 2. Logged-in users can use the Ctrl Alt Del shortcut key and select "Change Password" to operate directly; 3. Microsoft account users can change their passwords on the "Security" page of the official website of Microsoft account, and the system will automatically synchronize the next time they are connected to the Internet. Pay attention to the strength and effectiveness of the password to ensure security.
2025-07-17
comment 0
988

Level up your browsing with these five Safari tips
Article Introduction:Five practical tips to enhance Safari browsing experience
(This article has been updated and was first published on November 18, 2019)
Safari browser continues to improve, and Apple's default operating system browser adds new features every year, and if you don't know all of its features in a timely manner, you may miss some practical features. See if these advanced user tips can improve your efficiency in Safari browser.
1. Password strength check
Safari focuses on the security of your password. It will issue a warning if you detect that you are reusing the same password, or if the password is too short or too simple.
To perform a password security audit, start your browser, open the Safari menu, and select Preferences. Switch to the Password tab to view Sa
2025-02-25
comment 0
1073

Password Hashing in Python for Security
Article Introduction:Password hashing is used in Python to securely store user passwords. 1. Use libraries specially designed for passwords such as bcrypt or passlib for hashing, automatically add salt and support adaptive strength. 2. Avoid using fast hashing algorithms such as MD5 and SHA1, and do not splice manually or reuse salt values. 3. Store the complete hash string, including the algorithm identification and salt value. The field type is recommended to be VARCHAR(60) or above. 4. Do not encrypt the hash extra or set a unique index to ensure the security of password storage.
2025-07-24
comment 0
254

gate.io trading platform Apple version download and registration tutorial
Article Introduction:Article introduction: The download, installation and registration process of Gate.io Sesame Open Door on Apple phones. Before downloading, you need to confirm iOS 12 and above, network and Apple ID. Search and download the official application on the official website, and follow the prompts to verify and complete the download. When registering, open the application, fill in your email or mobile phone number, set a high-strength password and fund password, complete the registration after agreeing to the terms, and then verify your identity. Finally, it is recommended to enable two-factor verification to ensure the security of your account.
2025-03-04
comment 0
414

usstd trading app installation address usstd trading platform latest APP registration link
Article Introduction:This article provides the latest APP download and installation tutorial for usstd trading platform. First, click the official download link of Binance, Ouyi OKX, Huobi and Gate.io Sesame Open in the article. Secondly, after the download is completed, install it according to the prompts and enable the permission of the application from unknown sources in the settings; finally, when registering an account, fill in the mobile phone number or email address, set password, verify information, and agree to the agreement to complete the registration. It is also recommended to set a high-strength password and enable two-step verification to ensure account security.
2025-07-03
comment 0
639

okx web version login portal Ouyi OKX web version portal latest
Article Introduction:To log in to Ouyi OKX web version safely and efficiently, please follow the following steps: 1. Verify the official website, make sure to enter the correct domain name and add it to your favorites to prevent phishing; 2. Select the login method, support email/mobile phone number or third-party account login; 3. Enter the account password, it is recommended to set a high-strength password and change it regularly; 4. For identity verification, you can choose Google Verifier, SMS/mailbox verification code or biometrics; 5. Click the login button to complete login. After logging in, you can view your account balance, conduct transactions, recharge and withdraw cash, view records and set security functions. To ensure account security, two-step verification should be enabled, high-strength passwords should be set, phishing websites should be alert to account activities regularly, use a safe network environment, and use the platform to provide a reasonable use.
2025-06-12
comment 0
556

Official gate exchange entrance
Article Introduction:The safe methods to access the official Gate.io website include: 1. Get the latest links through official social media; 2. Use CoinMarketCap and other platforms to find official links; 3. Download the App from the official website. To ensure account security, you need to: 1. Enable two-factor verification; 2. Use a high-strength password; 3. Properly keep your private keys and mnemonics; 4. Regularly check transaction records.
2025-03-25
comment 0
909

Why can't I connect to WiFi?
Article Introduction:The problem of not being able to connect to WiFi can be checked through the following steps: 1. Check whether the router and device are normal, such as power on, indicator lights, WiFi switches; 2. Make sure the password is correct, pay attention to uppercase and uppercase, uppercase and lowercase characters; 3. Handle IP address conflicts, reconnect or set to DHCP mode; 4. Improve signal strength, get close to the router or use an extender.
2025-07-27
comment 0
714

How to switch from a Microsoft account to a local account in Windows
Article Introduction:It is actually not difficult to switch to a local account from a Microsoft account. The key is to confirm whether the Windows version supports it, back up the synchronization data in advance, and follow the steps. 1. Check the system version. The home version and the professional version generally support switching, and the enterprise version may be restricted by group policy; 2. Go to "Settings" → "Account" → "Your Information", click "Replace with Local Account"; 3. Verify the Microsoft account password and create a local account username, password and prompt; 4. After logging out, the file will not be lost, but the synchronization function will be interrupted. If you encounter "Cannot create a local account", you can check the network, duplicate username, password strength, or manually add an account using a command prompt. The impact after switching includes OneDrive synchronization interrupt and Microsoft Stor
2025-06-30
comment 0
366

How to create oracle database How to create oracle database
Article Introduction:To create an Oracle database, the common method is to use the dbca graphical tool. The steps are as follows: 1. Use the dbca tool to set the dbName to specify the database name; 2. Set sysPassword and systemPassword to strong passwords; 3. Set characterSet and nationalCharacterSet to AL32UTF8; 4. Set memorySize and tablespaceSize to adjust according to actual needs; 5. Specify the logFile path. Advanced methods are created manually using SQL commands, but are more complex and prone to errors. Pay attention to password strength, character set selection, tablespace size and memory
2025-04-11
comment 0
820



















