
This article has been updated. Originally published on April 26, 2021
Zoom's end-to-end (E2E) encryption is good news for those who care about online privacy and security. But this feature is not enabled by default, so you may still connect with friends, family and colleagues through a standard encryption protocol with less secure video call program.
Frankly, this...is OK, but you deserve the best.
Why should E2E encryption be enabled
Encrypted communication itself is just a bunch of incomprehensible characters, and a key is required to convert it into an understandable text message, audio clip or video call. The main differences between various encryption types are the locations of key generation, management and storage.
[Related: How to Safely Store and Share Sensitive Files]
For example, Zoom's default AES 256-bit GCM encryption generates a key on the company's own server. This means that the content of your team’s daily employee meetings is still transmitted from your device over the internet to your colleague’s laptop or cell phone in a secure way. But because Zoom controls the communication keys, they can theoretically decrypt the "funny" story you told about your cat - and your teammates are unresponsive to it. What's more serious is that it also means that anyone who gets access to Zoom servers — from hackers to government agencies — can see what you're talking about all the time.
By enabling E2E encryption, your device (and everyone's devices on the call) will generate, manage, and store your communication keys. This means that Zoom's servers only receive a bunch of incomprehensible code that they then directed it to their final destination. The company will never see what you say, the photos you share, or the stories you wish you could cancel.
Why is E2E encryption on Zoom not automatic
As of now, when you enable E2E encryption on Zoom, you automatically lose access to many other features. This includes the ability to join calls, cloud recording, live streaming and real-time transcription before the host. Other features, such as one-to-one private chat and meeting response, will be disabled based on the version of Zoom you are running.
There are other limitations in this feature. Only those using Zoom Rooms, desktop clients, or mobile applications can join E2E encrypted calls, while those dialed or connected through third-party clients such as Lync or Skype cannot join.
[Related: 6 Safe WhatsApp Alternatives]
When Zoom announced the arrival of E2E encryption in October, one of the benefits mentioned was that it can be used by both paid customers and users who use the app for free. But here is a trick: To use this new encryption method, free users must have a valid billing option in the file and verify their account. This means providing Zoom with credit card details and phone numbers, as well as a physical address, which can be a high price if you take your privacy seriously.
All of these warnings are why Zoom recommends that users enable E2E encryption only for sensitive communications (conferences that really require this extra layer of protection). However, since E2E encryption is the only online protocol that completely protects your online content, it should not be optional. It should be the default.
How to set E2E encryption on Zoom
On your computer, log in to the Zoom website and click Set . Under the Meetings tab, select Safe and scroll down to turn on the toggle next to Allow end-to-end encryption. When you do this, a new option to select the encryption type will appear below - select the circle next to
End-to-End Encryption. If you are not a paid user, the platform will require you to verify your account with a valid phone number. If you are managing a group of users or an entire enterprise account, it means similar. Before clicking Settings, click
User Management, and then click Group Management. You can find more details in Zoom's Help Center.
[Related: Best Zoom Tips and Add-ons for Video Chat]When E2E encryption is enabled, the next time you host a meeting, you will see the corresponding icon in the upper left corner of the screen - it looks like a green shield with a lock. Click it to check if E2E encryption is enabled, and then click
Verifyto ensure your communication is secure. When you do this, you will see a pop-up window containing eight sets of five digits. Once all guests are online, please open the same window. Read these numbers aloud and if they match, congratulations – you are now connected to the best security system on the internet.
Updated April 27 at 2:12 pm: This article has been updated to reflect that E2E encryption on Zoom is no longer a technical preview.The above is the detailed content of Secure your Zoom calls with end-to-end encryption. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 Windows Security is blank or not showing options
Jul 07, 2025 am 02:40 AM
Windows Security is blank or not showing options
Jul 07, 2025 am 02:40 AM
When the Windows Security Center is blank or the function is missing, you can follow the following steps to check: 1. Confirm whether the system version supports full functions, some functions of the Home Edition are limited, and the Professional Edition and above are more complete; 2. Restart the SecurityHealthService service to ensure that its startup type is set to automatic; 3. Check and uninstall third-party security software that may conflict; 4. Run the sfc/scannow and DISM commands to repair system files; 5. Try to reset or reinstall the Windows Security Center application, and contact Microsoft support if necessary.
 Windows stuck on 'undoing changes made to your computer'
Jul 05, 2025 am 02:51 AM
Windows stuck on 'undoing changes made to your computer'
Jul 05, 2025 am 02:51 AM
The computer is stuck in the "Undo Changes made to the computer" interface, which is a common problem after the Windows update fails. It is usually caused by the stuck rollback process and cannot enter the system normally. 1. First of all, you should wait patiently for a long enough time, especially after restarting, it may take more than 30 minutes to complete the rollback, and observe the hard disk light to determine whether it is still running. 2. If there is no progress for a long time, you can force shut down and enter the recovery environment (WinRE) multiple times, and try to start repair or system restore. 3. After entering safe mode, you can uninstall the most recent update records through the control panel. 4. Use the command prompt to execute the bootrec command in the recovery environment to repair the boot file, or run sfc/scannow to check the system file. 5. The last method is to use the "Reset this computer" function
 Proven Ways for Microsoft Teams Error 657rx in Windows 11/10
Jul 07, 2025 pm 12:25 PM
Proven Ways for Microsoft Teams Error 657rx in Windows 11/10
Jul 07, 2025 pm 12:25 PM
Encountering something went wrong 657rx can be frustrating when you log in to Microsoft Teams or Outlook. In this article on MiniTool, we will explore how to fix the Outlook/Microsoft Teams error 657rx so you can get your workflow back on track.Quick
 The RPC server is unavailable Windows
Jul 06, 2025 am 12:07 AM
The RPC server is unavailable Windows
Jul 06, 2025 am 12:07 AM
When encountering the "RPCserverisunavailable" problem, first confirm whether it is a local service exception or a network configuration problem. 1. Check and start the RPC service to ensure that its startup type is automatic. If it cannot be started, check the event log; 2. Check the network connection and firewall settings, test the firewall to turn off the firewall, check DNS resolution and network connectivity; 3. Run the sfc/scannow and DISM commands to repair the system files; 4. Check the group policy and domain controller status in the domain environment, and contact the IT department to assist in the processing. Gradually check it in sequence to locate and solve the problem.
 the default gateway is not available Windows
Jul 08, 2025 am 02:21 AM
the default gateway is not available Windows
Jul 08, 2025 am 02:21 AM
When you encounter the "DefaultGatewayisNotAvailable" prompt, it means that the computer cannot connect to the router or does not obtain the network address correctly. 1. First, restart the router and computer, wait for the router to fully start before trying to connect; 2. Check whether the IP address is set to automatically obtain, enter the network attribute to ensure that "Automatically obtain IP address" and "Automatically obtain DNS server address" are selected; 3. Run ipconfig/release and ipconfig/renew through the command prompt to release and re-acquire the IP address, and execute the netsh command to reset the network components if necessary; 4. Check the wireless network card driver, update or reinstall the driver to ensure that it works normally.
 How to fix 'SYSTEM_SERVICE_EXCEPTION' stop code in Windows
Jul 09, 2025 am 02:56 AM
How to fix 'SYSTEM_SERVICE_EXCEPTION' stop code in Windows
Jul 09, 2025 am 02:56 AM
When encountering the "SYSTEM_SERVICE_EXCEPTION" blue screen error, you do not need to reinstall the system or replace the hardware immediately. You can follow the following steps to check: 1. Update or roll back hardware drivers such as graphics cards, especially recently updated drivers; 2. Uninstall third-party antivirus software or system tools, and use WindowsDefender or well-known brand products to replace them; 3. Run sfc/scannow and DISM commands as administrator to repair system files; 4. Check memory problems, restore the default frequency and re-plug and unplug the memory stick, and use Windows memory diagnostic tools to detect. In most cases, the driver and software problems can be solved first.
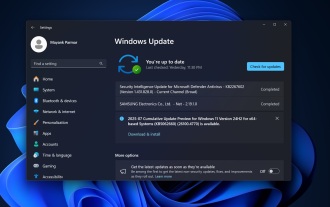 Windows 11 KB5062660 24H2 out with features, direct download links for offline installer (.msu)
Jul 23, 2025 am 09:43 AM
Windows 11 KB5062660 24H2 out with features, direct download links for offline installer (.msu)
Jul 23, 2025 am 09:43 AM
Windows 11 KB5062660 is now rolling out as an optional update for Windows 11 24H2 with a few new features, including Recall AI in Europe. This patch is available via Windows Update, but Microsoft has also posted direct download l
 How to repair Windows 11 using command prompt
Jul 05, 2025 am 02:59 AM
How to repair Windows 11 using command prompt
Jul 05, 2025 am 02:59 AM
How to use command prompt to repair Windows 11? 1. Enter the command prompt through the recovery environment: enter the recovery environment through USB boot or three consecutive interrupts, and then select Troubleshooting > Advanced Options > Command Prompt; 2. Use DISM to repair the system image: Run DISM/Online/Cleanup-Image/CheckHealth to check for corruption, DISM/Online/Cleanup-Image/ScanHealth scanning problem, DISM/Online/Cleanup-Image/RestoreHealth to repair the problem, and specify an external source if necessary; 3. Run SF






