 Database
Database
 Mysql Tutorial
Mysql Tutorial
 The command to create a data table in mysql is the standard table creation statement format
The command to create a data table in mysql is the standard table creation statement format
The command to create a data table in mysql is the standard table creation statement format
May 28, 2025 pm 06:36 PMThe standard command to create a data table in MySQL is CREATE TABLE. 1. The table name should be concise and use lowercase letters and underscores. 2. When defining a column, specify the data type and constraints, such as INT, VARCHAR, PRIMARY KEY, etc. 3. Use AUTO_INCREMENT and DEFAULT CURRENT_TIMESTAMP to optimize field settings. 4. Consider performance optimization and scalability, use indexes reasonably and select appropriate character sets and collation rules.

The standard command to create a data table in MySQL is CREATE TABLE . Let's start with this question and then dive into how to create data tables in MySQL, as well as some experiences and best practices in real-world applications.
In MySQL, the standard format for creating data tables is as follows:
CREATE TABLE table_name (
column1 datatype constraints,
column2 datatype constraints,
column3 datatype constraints,
....
);This format looks simple, but there are many details to consider in actual operation. Let's talk about this process in detail, as well as some of the experience I have accumulated in actual projects.
First, we need to name the table. Table names should be concise and clear, and words are usually split using lowercase letters and underscores, which is done to avoid problems in different operating systems and database management tools. I like to use names like users , products , not UserTable or PRODUCTS .
Next is to define the column. Each column needs to specify a data type, such as INT , VARCHAR , DATETIME , etc. Here is a tip: If you are not sure about the length of a certain field, you can first set a larger length, such as VARCHAR(255) , and then adjust it according to the actual data later. MySQL optimizes storage space based on the actual stored data, but setting a larger length at the beginning can avoid frequent modification of the table structure.
When defining columns, you should also consider whether you need to set some constraints, such as PRIMARY KEY , UNIQUE , NOT NULL , etc. These constraints can help us maintain data integrity and consistency. For example, I like to set the email field to UNIQUE in the user table, so that each user's email address is unique.
CREATE TABLE users (
id INT AUTO_INCREMENT PRIMARY KEY,
username VARCHAR(50) NOT NULL,
email VARCHAR(255) UNIQUE NOT NULL,
created_at DATETIME DEFAULT CURRENT_TIMESTAMP
); The above code shows a simple user table creation statement. Note that I used AUTO_INCREMENT to automatically increment id , which can avoid manually maintaining the value of the primary key. DEFAULT CURRENT_TIMESTAMP lets created_at field automatically fill in the current time, which is very useful in many scenarios.
In actual projects, some performance optimizations and best practices need to be considered when creating data tables. For example, using indexes reasonably can greatly improve query efficiency, but I suggest adding indexes when the actual data volume is large, because indexes will increase the overhead of insertion and update. In addition, the design of the table should take into account future scalability and try to avoid frequent modification of the table structure.
Another point that is easy to ignore is character sets and sorting rules. When creating a table, you can specify the character set and collation rules, such as:
CREATE TABLE posts (
id INT AUTO_INCREMENT PRIMARY KEY,
title VARCHAR(255) NOT NULL,
content TEXT NOT NULL
) CHARSET=utf8mb4 COLLATE=utf8mb4_unicode_ci;This ensures that the table supports special characters such as emoji and is case-insensitive when sorting.
In actual operation, I have also encountered some common mistakes. For example, forgetting to set NOT NULL constraints will result in incomplete data; or not taking into account existing data when modifying the table structure, resulting in the modification failure. These problems can be avoided by careful planning and testing.
In short, although the standard commands for creating data tables in MySQL are simple, there are many details and best practices to consider in actual operation. By rationally designing the table structure, using constraints and indexing, and taking into account performance optimization, we can create efficient and easy-to-maintain data tables.
The above is the detailed content of The command to create a data table in mysql is the standard table creation statement format. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 Mastering Flow Control Within foreach Using break, continue, and goto
Aug 06, 2025 pm 02:14 PM
Mastering Flow Control Within foreach Using break, continue, and goto
Aug 06, 2025 pm 02:14 PM
breakexitstheloopimmediatelyafterfindingatarget,idealforstoppingatthefirstmatch.2.continueskipsthecurrentiteration,usefulforfilteringitemsliketemporaryfiles.3.gotojumpstoalabeledstatement,acceptableinrarecaseslikecleanuporerrorhandlingbutshouldbeused
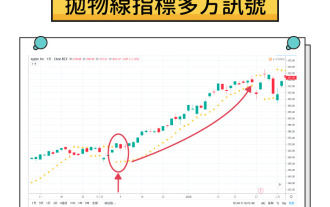 What is a parabolic SAR indicator? How does SAR indicator work? Comprehensive introduction to SAR indicators
Aug 06, 2025 pm 08:12 PM
What is a parabolic SAR indicator? How does SAR indicator work? Comprehensive introduction to SAR indicators
Aug 06, 2025 pm 08:12 PM
Contents Understand the mechanism of parabola SAR The working principle of parabola SAR calculation method and acceleration factor visual representation on trading charts Application of parabola SAR in cryptocurrency markets1. Identify potential trend reversal 2. Determine the best entry and exit points3. Set dynamic stop loss order case study: hypothetical ETH trading scenario Parabola SAR trading signals and interpretation Based on parabola SAR trading execution Combining parabola SAR with other indicators1. Use moving averages to confirm trend 2. Relative strength indicator (RSI) for momentum analysis3. Bollinger bands for volatility analysis Advantages of parabola SAR and limitations Advantages of parabola SAR
 Solana (SOL Coin) Price Forecast: 2025-2030 and Future Outlook
Aug 06, 2025 pm 08:42 PM
Solana (SOL Coin) Price Forecast: 2025-2030 and Future Outlook
Aug 06, 2025 pm 08:42 PM
Table of Contents Solana's Price History and Important Market Data Important Data in Solana Price Chart: 2025 Solana Price Forecast: Optimistic 2026 Solana Price Forecast: Maintain Trend 2026 Solana Price Forecast: 2030 Solana Long-term Price Forecast: Top Blockchain? What affects the forecast of sun prices? Scalability and Solana: Competitive Advantages Should you invest in Solana in the next few years? Conclusion: Solana's price prospects Conclusion: Solana has its excellent scalability, low transaction costs and high efficiency
 Blockchain browser: a must-have tool for querying digital currency transaction information
Aug 06, 2025 pm 11:27 PM
Blockchain browser: a must-have tool for querying digital currency transaction information
Aug 06, 2025 pm 11:27 PM
Blockchain browser is a necessary tool for querying digital currency transaction information. It provides a visual interface for blockchain data, so that users can query transaction hash, block height, address balance and other information; its working principle includes data synchronization, parsing, indexing and user interface display; core functions cover querying transaction details, block information, address balance, token data and network status; when using it, you need to obtain TxID and select the corresponding blockchain browser such as Etherscan or Blockchain.com to search; query address information to view balance and transaction history by entering the address; mainstream browsers include Bitcoin's Blockchain.com, Ethereum's Etherscan.io, B
 Can you explain method overloading and method overriding in Java?
Aug 06, 2025 am 07:41 AM
Can you explain method overloading and method overriding in Java?
Aug 06, 2025 am 07:41 AM
Method overloading and method overloading are two mechanisms for implementing polymorphism in Java. 1. Method overload occurs in the same class. It requires the same method name but different parameter list (number, type or order of parameters), which belongs to compile-time polymorphism. The return type can be different but cannot be overloaded by the return type alone. There can be different access modifiers and exception declarations; 2. Method rewriting occurs in the inheritance relationship. The subclass provides the specific implementation of the existing methods of the parent class. It requires the same method signature and the return type is compatible. The access modifier cannot be more strict. It belongs to the runtime polymorphism. The instance method must be used and the correct rewrite can be ensured through the @Override annotation. Together, the two improve code readability and scalability.
 go by example running a subprocess
Aug 06, 2025 am 09:05 AM
go by example running a subprocess
Aug 06, 2025 am 09:05 AM
Run the child process using the os/exec package, create the command through exec.Command but not execute it immediately; 2. Run the command with .Output() and catch stdout. If the exit code is non-zero, return exec.ExitError; 3. Use .Start() to start the process without blocking, combine with .StdoutPipe() to stream output in real time; 4. Enter data into the process through .StdinPipe(), and after writing, you need to close the pipeline and call .Wait() to wait for the end; 5. Exec.ExitError must be processed to get the exit code and stderr of the failed command to avoid zombie processes.
 From blockchain to cryptocurrency, a complete analysis of basic concepts
Aug 06, 2025 pm 11:51 PM
From blockchain to cryptocurrency, a complete analysis of basic concepts
Aug 06, 2025 pm 11:51 PM
Blockchain is a distributed and decentralized digital ledger technology. Its core principles include: 1. Distributed ledger ensures that data is stored simultaneously on all nodes; 2. Encryption technology, linking blocks through hash values to ensure that data is not tampered with; 3. Consensus mechanisms, such as PoW or PoS, ensure that transactions are agreed between nodes; 4. Decentralization, eliminating single point of control, enhancing censorship resistance; 5. Smart contracts, protocols for automated execution. Cryptocurrencies are digital assets issued based on blockchain. The operation process is: 1. The user initiates transactions and signs digitally; 2. The transactions are broadcast to the network; 3. The miner or verifier verifies the validity of the transaction; 4. Multiple transactions are packaged into new blocks; 5. Confirm the new zone through consensus mechanism
 The top ten currency trading platforms in the world, the top ten trading software apps in the currency circle
Aug 06, 2025 pm 11:42 PM
The top ten currency trading platforms in the world, the top ten trading software apps in the currency circle
Aug 06, 2025 pm 11:42 PM
Binance: is known for its high liquidity, multi-currency support, diversified trading modes and powerful security systems; 2. OKX: provides diversified trading products, layout DeFi and NFT, and has a high-performance matching engine; 3. Huobi: deeply engaged in the Asian market, pays attention to compliance operations, and provides professional services; 4. Coinbase: strong compliance, friendly interface, suitable for novices and is a listed company; 5. Kraken: strict security measures, supports multiple fiat currencies, and has high transparency; 6. Bybit: focuses on derivative trading, low latency, and complete risk control; 7. KuCoin: rich currency, supports emerging projects, and can enjoy dividends with KCS; 8. Gate.io: frequent new coins, with Copy Tr





