 web3.0
web3.0
 Buterin shares a research article on fully homomorphic encryption: What is FHE and can it solve Web3 privacy problems?
Buterin shares a research article on fully homomorphic encryption: What is FHE and can it solve Web3 privacy problems?
Buterin shares a research article on fully homomorphic encryption: What is FHE and can it solve Web3 privacy problems?
May 06, 2024 pm 07:00 PM
Vitalik Buterin, the co-founder of Ethereum, has frequently talked about privacy issues recently, first for the privacy protocol Railgun, and after the U.S. Congress approved a controversial issue in the Foreign Intelligence Surveillance Act last month. After extending the terms for two years and authorizing U.S. intelligence agencies to monitor foreign targets without a search warrant, he criticized the value of cryptocurrency for being under attack.
Vitalik Buterin tweeted on the 5th that many people have recently been interested in fully homomorphic encryption (Fully homomophic Encryption, FHE) technology. Therefore, he republished his article published in 2020, which went into depth. The relevant mathematical working principles of FHE are introduced.
FHE Introduction
Vitalik Buterin pointed out in this article that FHE has long been considered one of the holy grails of cryptography. FHE is an encryption technology that allows third parties to perform calculations on encrypted materials. , and obtain the encrypted result, which the third party can return to anyone who has the decryption key of the original material, but the third party itself cannot decrypt the material or the result itself.
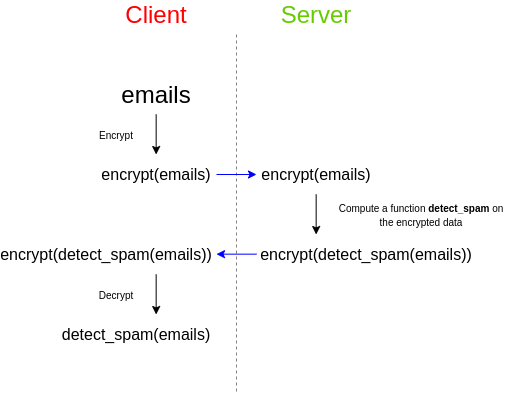
Vitalik Buterin pointed out as an example that a user receives a series of emails and wants to use a third-party spam filter to check whether they are spam.
Generally speaking, spam filters will want to protect the privacy of the algorithm. Either the spam filter provider wants its source code to be closed source, or it will rely on a very large database, and the provider does not want to make this public. Database, because this will make attacks easier, but users who are concerned about the privacy of their data and do not want to upload their unencrypted emails to third parties can use FHE to achieve this.
FHE is widely used
The article mentioned that FHE is widely used, covering the blockchain field, such as light clients that can be used to protect privacy end, the following applications can also be implemented:
More efficient covert address protocols, and more general scalability solutions for privacy protection protocols. The current privacy protection protocol requires each user Scan the entire blockchain yourself for incoming transactions.
A privacy-preserving data sharing marketplace that allows users to perform specific calculations on their data while maintaining full control over their data.
As part of stronger cryptographic primitives, such as more efficient multi-party computation protocols, program obfuscation may eventually also be covered.
What are the differences between FHE, ZK and MPC?
Previously, Portal Ventures wrote an article last year to discuss FHE technology, analyzing its differences with zero-knowledge proof (ZK) and multi-party computation (MPC), pointing out that in the field of cryptocurrency, FHE can be used to build a more private For smart contracts and other blockchain applications, ZK is used to build scalable blockchain solutions, while MPC is mainly used for private key management and custody.
The article mentioned that although FHE, ZK and MPC overlap in some aspects, they all have their own unique advantages and application scenarios. In the currency circle, these three technologies are all for enhancing privacy and The security offers huge potential, but their combination and further research remains an active area in the crypto community.
The above is the detailed content of Buterin shares a research article on fully homomorphic encryption: What is FHE and can it solve Web3 privacy problems?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to get stablecoin USDT for free_Xiaobai stablecoin USDT obtain guide
Jul 15, 2025 pm 11:51 PM
How to get stablecoin USDT for free_Xiaobai stablecoin USDT obtain guide
Jul 15, 2025 pm 11:51 PM
Yes, you can get USDT for free in the following 5 ways: 1. Participate in airdrop tasks on mainstream exchanges, such as registering and giving away, completing novice tasks, and inviting friends to get rewards; 2. Join the blockchain project community and obtain airdrops through Web3 social platform or Twitter/Discord interaction; 3. Participate in the "test network" activity, register the test chain address and simulate the use of DApp to get incentives; 4. Complete tasks on the cryptocurrency navigation platform to receive novice gift packages, participate in sign-in, lottery and other activities; 5. Interact with the content creation and community, and publish original content to obtain USDT rewards from the project party. At the same time, you need to pay attention to security risks, do not fill in private keys, do not believe in scams, and choose mainstream platforms to participate.
 LayerZero, StarkNet, ZK Ecological Preheat: How long can the airdrop bonus last?
Jul 16, 2025 am 10:06 AM
LayerZero, StarkNet, ZK Ecological Preheat: How long can the airdrop bonus last?
Jul 16, 2025 am 10:06 AM
The duration of the airdrop dividend is uncertain, but the LayerZero, StarkNet and ZK ecosystems still have long-term value. 1. LayerZero achieves cross-chain interoperability through lightweight protocols; 2. StarkNet provides efficient and low-cost Ethereum L2 expansion solutions based on ZK-STARKs technology; 3. ZK ecosystem (such as zkSync, Scroll, etc.) expands the application of zero-knowledge proof in scaling and privacy protection; 4. Participation methods include the use of bridging tools, interactive DApps, participating test networks, pledged assets, etc., aiming to experience the next generation of blockchain infrastructure in advance and strive for potential airdrop opportunities.
 The role of Ethereum smart contracts
Jul 15, 2025 pm 09:18 PM
The role of Ethereum smart contracts
Jul 15, 2025 pm 09:18 PM
The role of Ethereum smart contract is to realize decentralized, automated and transparent protocol execution. Its core functions include: 1. As the core logic layer of DApp, it supports token issuance, DeFi, NFT and other functions; 2. Automatically execute contracts through code to reduce the risks of human intervention and fraud; 3. Build a DeFi ecosystem so that users can directly conduct financial operations such as lending and transactions; 4. Create and manage digital assets to ensure uniqueness and verifiability; 5. Improve the transparency and security of supply chain and identity verification; 6. Support DAO governance and realize decentralized decision-making.
 How to identify fake altcoins? Teach you to avoid cryptocurrency fraud
Jul 15, 2025 pm 10:36 PM
How to identify fake altcoins? Teach you to avoid cryptocurrency fraud
Jul 15, 2025 pm 10:36 PM
To identify fake altcoins, you need to start from six aspects. 1. Check and verify the background of the materials and project, including white papers, official websites, code open source addresses and team transparency; 2. Observe the online platform and give priority to mainstream exchanges; 3. Beware of high returns and people-pulling modes to avoid fund traps; 4. Analyze the contract code and token mechanism to check whether there are malicious functions; 5. Review community and media operations to identify false popularity; 6. Follow practical anti-fraud suggestions, such as not believing in recommendations or using professional wallets. The above steps can effectively avoid scams and protect asset security.
 Solana, Toncoin, and AI tokens collectively explode: has the horn of the bull market sounded?
Jul 16, 2025 am 10:09 AM
Solana, Toncoin, and AI tokens collectively explode: has the horn of the bull market sounded?
Jul 16, 2025 am 10:09 AM
Yes, the crypto market is ushering in signs of a full-scale bull market. After Bitcoin hit a record high recently, Solana (SOL), Toncoin (TON) and AI-related tokens have collectively surged, showing a sharp rise in market heat; 1. Solana was driven by large-scale institutional buying, Meme coin boom and ecological recovery, and its price exceeded US$200; 2. Toncoin relies on Telegram's huge user base and practical application scenarios, and set a new high; 3. AI tokens benefit from the catalysis of technology trends and the NVIDIA GTC conference to attract funds to make arrangements in advance; in summary, the rising market with multiple points is driven by fundamentals and is regarded as a signal of a bull market, but investors still need to be wary of volatility risks and pay attention to long-term value.
 The flow of funds on the chain is exposed: What new tokens are being bet on by Clever Money?
Jul 16, 2025 am 10:15 AM
The flow of funds on the chain is exposed: What new tokens are being bet on by Clever Money?
Jul 16, 2025 am 10:15 AM
Ordinary investors can discover potential tokens by tracking "smart money", which are high-profit addresses, and paying attention to their trends can provide leading indicators. 1. Use tools such as Nansen and Arkham Intelligence to analyze the data on the chain to view the buying and holdings of smart money; 2. Use Dune Analytics to obtain community-created dashboards to monitor the flow of funds; 3. Follow platforms such as Lookonchain to obtain real-time intelligence. Recently, Cangming Money is planning to re-polize LRT track, DePIN project, modular ecosystem and RWA protocol. For example, a certain LRT protocol has obtained a large amount of early deposits, a certain DePIN project has been accumulated continuously, a certain game public chain has been supported by the industry treasury, and a certain RWA protocol has attracted institutions to enter.
 Which is better, DAI or USDC?_Is DAI suitable for long-term holding?
Jul 15, 2025 pm 11:18 PM
Which is better, DAI or USDC?_Is DAI suitable for long-term holding?
Jul 15, 2025 pm 11:18 PM
Is DAI suitable for long-term holding? The answer depends on individual needs and risk preferences. 1. DAI is a decentralized stablecoin, generated by excessive collateral for crypto assets, suitable for users who pursue censorship resistance and transparency; 2. Its stability is slightly inferior to USDC, and may experience slight deansal due to collateral fluctuations; 3. Applicable to lending, pledge and governance scenarios in the DeFi ecosystem; 4. Pay attention to the upgrade and governance risks of MakerDAO system. If you pursue high stability and compliance guarantees, it is recommended to choose USDC; if you attach importance to the concept of decentralization and actively participate in DeFi applications, DAI has long-term value. The combination of the two can also improve the security and flexibility of asset allocation.
 Who is suitable for stablecoin DAI_ Analysis of decentralized stablecoin usage scenarios
Jul 15, 2025 pm 11:27 PM
Who is suitable for stablecoin DAI_ Analysis of decentralized stablecoin usage scenarios
Jul 15, 2025 pm 11:27 PM
DAI is suitable for users who attach importance to the concept of decentralization, actively participate in the DeFi ecosystem, need cross-chain asset liquidity, and pursue asset transparency and autonomy. 1. Supporters of the decentralization concept trust smart contracts and community governance; 2. DeFi users can be used for lending, pledge, and liquidity mining; 3. Cross-chain users can achieve flexible transfer of multi-chain assets; 4. Governance participants can influence system decisions through voting. Its main scenarios include decentralized lending, asset hedging, liquidity mining, cross-border payments and community governance. At the same time, it is necessary to pay attention to system risks, mortgage fluctuations risks and technical threshold issues.




