 Mobile Game Tutorial
Mobile Game Tutorial
 Mobile Game Guide
Mobile Game Guide
 How to access DeepSeekapi - DeepSeekapi access call tutorial
How to access DeepSeekapi - DeepSeekapi access call tutorial
How to access DeepSeekapi - DeepSeekapi access call tutorial
Mar 12, 2025 pm 12:24 PMDetailed explanation of DeepSeek API access and call: Quick guide
This article will provide you with detailed instructions on how to access and call the DeepSeek API, helping you easily use powerful AI models.

Step 1: Obtain the API key
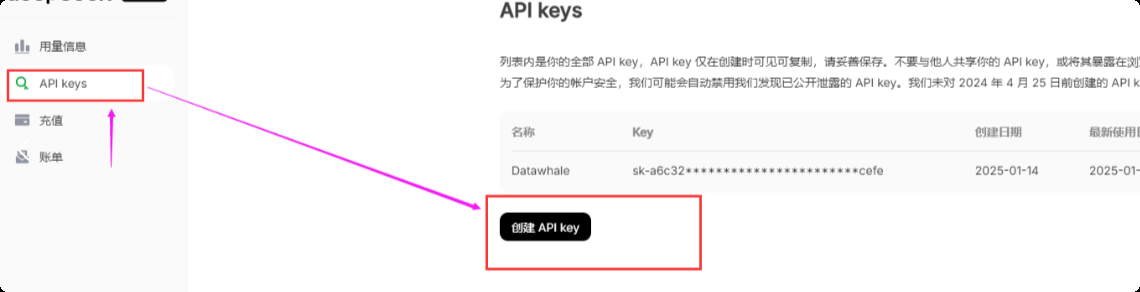
- Visit the DeepSeek official website and click on the "Open Platform" in the upper right corner.

You will get a certain number of free tokens (for metering API usage). In the menu on the left, click "API Keys" and then click "Create API key".
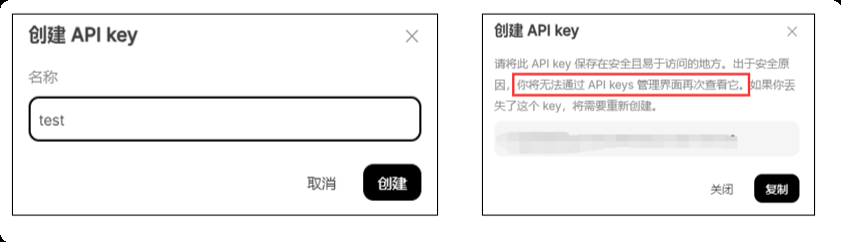
Name your API key (for example, "test") and copy the generated key immediately. Be sure to save this key properly as it will only be displayed once.
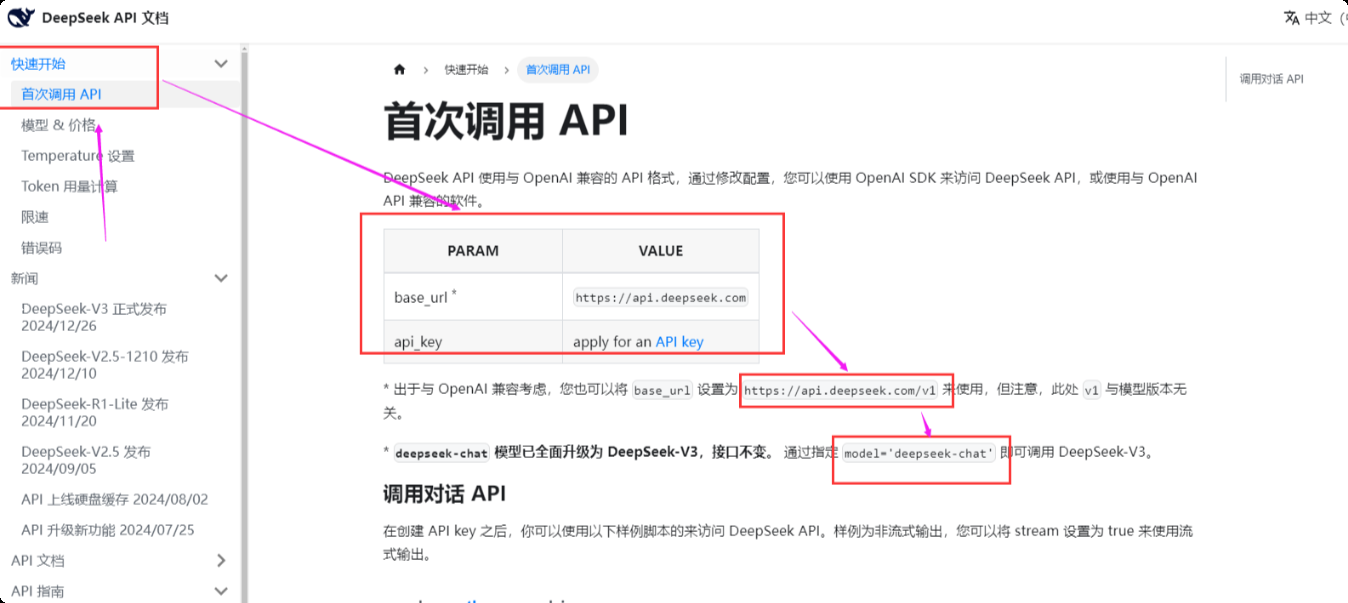
Step 2: Get base_url and chat_model
- In the Quick Start section of the DeepSeek API documentation, find
base_urlandchat_modelparameters. The acquisition methods of other platforms are similar.
Step 3: Configure model parameters
For security reasons, it is recommended to store the API key in environment variables rather than writing directly into the code. The following two methods are provided:
Method 1: The terminal temporarily sets environment variables (only valid in the current terminal session)
Enter the following command in the terminal to add your API key to the environment variable (replace YOUR_API_KEY with your actual key):
export API_KEY="YOUR_API_KEY"
Method 2: Create .env file (recommended)
- Create a file named
.env. - Add the following in the
.envfile, replacingYOUR_API_KEYwith your actual key:
<code>API_KEY="YOUR_API_KEY"</code>
In Python code, use the python-dotenv library to read environment variables:
from dotenv import load_dotenv
import os
load_dotenv() # Load the .env file api_key = os.getenv("API_KEY")
Step 4: Create a client
Create a DeepSeek client using base_url and api_key . (The specific client creation method depends on the library you are using)
Step 5: Test API calls
Here is a simple Python code example for testing API connections:
# ... (Previous code, including client creation) ...
response = client.chat(model=chat_model, messages=[{"role": "user", "content": "Hello"}])
print(response)
If everything is configured correctly, you will receive a reply from the model. If an error occurs, check that your API key and configuration are correct.
For more details, please refer to the official DeepSeek document. Original link (please replace it with the actual link)
The above is the detailed content of How to access DeepSeekapi - DeepSeekapi access call tutorial. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 Blockchain browser: a must-have tool for querying digital currency transaction information
Aug 06, 2025 pm 11:27 PM
Blockchain browser: a must-have tool for querying digital currency transaction information
Aug 06, 2025 pm 11:27 PM
Blockchain browser is a necessary tool for querying digital currency transaction information. It provides a visual interface for blockchain data, so that users can query transaction hash, block height, address balance and other information; its working principle includes data synchronization, parsing, indexing and user interface display; core functions cover querying transaction details, block information, address balance, token data and network status; when using it, you need to obtain TxID and select the corresponding blockchain browser such as Etherscan or Blockchain.com to search; query address information to view balance and transaction history by entering the address; mainstream browsers include Bitcoin's Blockchain.com, Ethereum's Etherscan.io, B
 From blockchain to cryptocurrency, a complete analysis of basic concepts
Aug 06, 2025 pm 11:51 PM
From blockchain to cryptocurrency, a complete analysis of basic concepts
Aug 06, 2025 pm 11:51 PM
Blockchain is a distributed and decentralized digital ledger technology. Its core principles include: 1. Distributed ledger ensures that data is stored simultaneously on all nodes; 2. Encryption technology, linking blocks through hash values to ensure that data is not tampered with; 3. Consensus mechanisms, such as PoW or PoS, ensure that transactions are agreed between nodes; 4. Decentralization, eliminating single point of control, enhancing censorship resistance; 5. Smart contracts, protocols for automated execution. Cryptocurrencies are digital assets issued based on blockchain. The operation process is: 1. The user initiates transactions and signs digitally; 2. The transactions are broadcast to the network; 3. The miner or verifier verifies the validity of the transaction; 4. Multiple transactions are packaged into new blocks; 5. Confirm the new zone through consensus mechanism
 Ethereum, a blockchain platform that surpasses Bitcoin, with advantages and innovation inventory
Aug 06, 2025 pm 11:57 PM
Ethereum, a blockchain platform that surpasses Bitcoin, with advantages and innovation inventory
Aug 06, 2025 pm 11:57 PM
Through its Turing-complete smart contracts, EVM virtual machines and Gas mechanisms, Ethereum has built a programmable blockchain platform beyond Bitcoin, supporting diversified application ecosystems such as DeFi and NFT; its core advantages include a rich DApp ecosystem, strong programmability, active developer community and cross-chain interoperability; it is currently implementing consensus transformation from PoW to PoS through the upgrade of Ethereum 2.0, introducing beacon chains, verifier mechanisms and punishment systems to improve energy efficiency, security and decentralization; in the future, it will rely on sharding technology to realize data sharding and parallel processing, greatly improving throughput; at the same time, Rollup technology has been widely used as a Layer 2 solution, Optimistic Rollup and ZK-Rollu
 What are common strategies for debugging a memory leak in Python?
Aug 06, 2025 pm 01:43 PM
What are common strategies for debugging a memory leak in Python?
Aug 06, 2025 pm 01:43 PM
Usetracemalloctotrackmemoryallocationsandidentifyhigh-memorylines;2.Monitorobjectcountswithgcandobjgraphtodetectgrowingobjecttypes;3.Inspectreferencecyclesandlong-livedreferencesusingobjgraph.show_backrefsandcheckforuncollectedcycles;4.Usememory_prof
 How to use the logging module for logging in Python?
Aug 06, 2025 am 09:40 AM
How to use the logging module for logging in Python?
Aug 06, 2025 am 09:40 AM
Python's logging module effectively tracks program events by flexibly configuring log levels, formats, and output targets. 1. Use logging.basicConfig() to quickly configure basic logs, but only the first call is valid; 2. Large applications should use logging.getLogger(__name__) to create named loggers to track the source; 3. Logs can be written to files through FileHandler; 4. Supports multiprocessors, such as output to files and consoles at the same time, and sets different levels respectively; 5. Log levels from low to high are DEBUG, INFO, WARNING, ERROR, CRITICAL, and sets visibility as needed; 6. Best practical
 How to implement a custom iterator within a Python class?
Aug 06, 2025 pm 01:17 PM
How to implement a custom iterator within a Python class?
Aug 06, 2025 pm 01:17 PM
Define__iter__()toreturntheiteratorobject,typicallyselforaseparateiteratorinstance.2.Define__next__()toreturnthenextvalueandraiseStopIterationwhenexhausted.Tocreateareusablecustomiterator,managestatewithin__iter__()oruseaseparateiteratorclass,ensurin
 What is MOMOFUN (MM coin)? How does it work? Introduction to the operating principle of MM coin, token economics and future development
Aug 06, 2025 pm 07:48 PM
What is MOMOFUN (MM coin)? How does it work? Introduction to the operating principle of MM coin, token economics and future development
Aug 06, 2025 pm 07:48 PM
Table of Contents MOMOFUN Price Analysis What is MOMOFUN? AI-powered AI agent AI pool provides intelligent liquidity technology backbone: How the MemeFi model of ELIZA framework MOMOFUN works MOMOFUN's future MOMOFUN price analysis**Price**0.003709**Market value**29,533,834**Circulation supply**7,800,000,000 mm**Total supply**30,000,000,000 mm MM tokens (total supply 30 billion) assumes multiple key functions in the system ecosystem: Governance and voting (
 How to connect to a Redis datastore from a Python application?
Aug 06, 2025 am 05:51 AM
How to connect to a Redis datastore from a Python application?
Aug 06, 2025 am 05:51 AM
Installtheredispackageusingpipinstallredis.2.ConnecttoRedisusingredis.Redis(host,port,db,decode_responses=True)forlocalorremoteservers,providingcredentialsifneeded.3.Alternatively,useredis.from_url()withaRedisURL,includingrediss://forSSLconnections.4





